Cloud Forensic Analysis - Unlocking Digital Evidence in the Cloud
Cloud forensic analysis is crucial for investigating digital crimes involving cloud environments. This guide covers the basics, including the types of data analyzed, the phases of investigation, and the unique challenges faced.

Understanding the Basics of Cloud Forensic Analysis
What is Cloud Forensic Analysis and How is it Different from Traditional Digital Forensics?
As an expert in this field, I often get asked about cloud forensics analysis. Everyone gets confused when they hear that forensics exists in the digital world, especially in the cloud. So, I will explain the basics of cloud forensics.
Cloud forensic analysis is a branch of digital forensics that specifically focuses on the analysis and investigation of data stored in cloud environments. Traditional digital forensics, in contrast, primarily deals with the collection and analysis of data stored on physical devices such as hard drives, computers, and mobile phones. Cloud forensic analysis addresses data stored on remote servers distributed by cloud service providers (CSPs). Some of the most well-known CSPs include Google Cloud, AWS, and Microsoft Azure.
Here are a few key differences between cloud forensics and traditional digital forensics:
Data Location: In traditional forensics, data is mainly stored locally. In cloud forensics, data is distributed across various servers in multiple data centers, often around the world.
Data Access: In traditional forensics, the forensic analyst has direct access to physical devices. In cloud forensics, circumstances are a bit more complicated. Access to data can be limited by CSP policies and procedures. Such circumstances often require legal warrants or special permissions.
Dynamic Environments: Cloud environments are dynamic and scalable, so resources can quickly change, be added, or removed. This can further complicate forensic analysis as it is very difficult to preserve traces.
Multitenancy: In cloud environments, resources are often shared among multiple users (tenants). This can pose a challenge in isolating data for a specific user.
Logs and Records: Cloud services generate logs and records which are often the main source of key information in forensics. These logs can include access information, user activities, and system events. They are often very extensive and complex, making them difficult to analyze.
Cloud forensic analysis requires specific tools and techniques that are tailored to the cloud environment. Cooperation with CSPs is indispensable in this type of forensics.
What Types of Data are Analyzed in Cloud Forensic Analysis?
In cloud forensics, different types of data are analyzed. These data are crucial for finding evidence and reconstructing events.
Data Analyzed in Cloud Forensic Analysis Include:
User Data: These are the data users store in the cloud. This includes files, documents, databases, and application data. By analyzing user data, we can detect unauthorized access or data modification.
Logs: These are a critical source of data in cloud forensics, including:
Access Logs: Record information about who accessed which resources and when.
Audit Logs: Record changes in system configuration, user permissions, and other key actions.
Event Logs: Record certain system events such as errors, warnings, successful/unsuccessful operations.
Application Logs: Contain records specific to the application used in the cloud environment.
Configuration Settings: Settings that define how resources in the cloud are configured and used. By analyzing these settings, we can identify potential security lapses and unauthorized changes that could lead to an incident.
Metadata: Represent information about the data, such as creation and modification dates, authors, and permissions. These data can help us uncover time frames and participants in events.
Virtual Machine Snapshots: Snapshots of virtual machines can contain complete system images at a given point in time, including all installed applications, the operating system, and data. These snapshots can help us analyze the system before and after an incident.
Network Traffic: Data about network traffic and packets that passed through the network. This data can help us identify unauthorized activities, such as hacking attempts or data transfers.
Service-Specific Data: Data specific to certain cloud services. This includes email services, storage services, or database services. For example, by analyzing email correspondence or database transactions, we can uncover key evidence.
User Activity Records: Records of user activities, including logins, password changes, resource usage, and other activities performed by users in the cloud environment.
Each of these types of data can provide important information for forensic investigation. Often, it is necessary to combine the analysis of multiple types of data to get a complete picture of events.
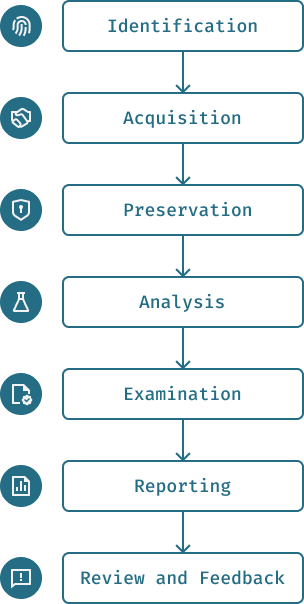
Process of Cloud Forensic Analysis
There are specific key phases in cloud forensic that we must adhere to during an investigation. It's not as simple as it seems; there are clear phases and protocols to follow. This is crucial to successfully collect and preserve evidence. So, if you want to conduct a successful analysis, be prepared to adhere to the following phases:
Identification
Identification of relevant data sources: First, it is necessary to determine which data and resources need to be analyzed. From experience, I can tell you that you will be dealing with user accounts, logs, databases, virtual machines, etc.
Identification of potential evidence: Recognizing the data that could be useful for the investigation. For example, access logs, configuration files, and user data.
Acquisition
Data collection: It is important to safely collect data at the right time. We must not allow data loss or alteration at any time. Since we need to collect data from a remote server, this can require a bit more effort.
Verification of data integrity: Using cryptographic hash functions (such as MD5 or SHA-256) to verify the integrity of collected data and ensure it has not been altered during collection.
Preservation
Evidence preservation: Ensuring that all data remains unchanged during the investigation. It's like putting a yellow tape at a crime scene. Therefore, we need to create copies and store the original data in a safe place.
Process documentation: In this phase, all steps taken during data collection and preservation are recorded to ensure an audit trail and the ability to reconstruct the process if needed.
Analysis
Analysis of collected data: Conducting a detailed analysis of the collected data to gather relevant evidence and successfully reconstruct events. This phase typically involves log analysis, file review, and identification of suspicious activities.
Data correlation: In this phase, we correlate multiple data sources to get a complete picture of the incident. For example, linking access logs with configuration changes and user activities.
Examination
Detailed examination of evidence: Focused analysis of specific evidence identified during the analysis phase. This can include file review, data decoding, and network traffic examination.
Extraction of useful information: Identifying key information relevant to the case, such as user identities, event timeframes, and methods used for unauthorized access.
Reporting
Report creation: Compiling a detailed report documenting all investigation findings, including methodology, collected evidence, analysis, and conclusions. The report should be clear, precise, and easily understandable for all interested parties.
Presentation of findings: Presenting key findings to relevant parties, such as legal teams, management, or other stakeholders. This may also include preparation for testimony in legal proceedings.
Review and Feedback
Process evaluation: Reviewing the entire forensic process to identify potential areas for improvement. This can include evaluating the tools, methods, and procedures used.
Procedure enhancement: Updating and improving forensic procedures and practices based on feedback and lessons learned during the investigation.
Each of these phases is critical for successfully conducting a cloud forensic investigation and ensuring the integrity and validity of collected evidence.
Collecting Data from Cloud Environments Using APIs
Collecting data from cloud environments is often done using APIs provided by cloud service providers. For example, a forensic investigator can use APIs to automate the collection of access logs and virtual machine snapshots. Imagine a detective at a crime scene taking out a special tool from his kit to detect invisible fingerprints. Similarly, a forensic engineer uses tools and APIs to safely retrieve data from the cloud without disrupting the system.
Challenges of Cloud Forensic Analysis
How does the distributed nature of cloud storage impact forensic investigations?
The distributed nature of cloud storage complicates cloud forensic analysis because data can be spread across multiple servers and locations worldwide. This makes it challenging to identify and collect all relevant evidence, necessitating specific tools and techniques to search and correlate data from various sources. It's akin to searching for puzzle pieces scattered across different cities. The forensic investigator must carefully coordinate the collection and analysis to obtain a comprehensive understanding of the events.
What Legal and Regulatory Considerations Arise in Cloud Forensic?
When collecting evidence from the cloud, it is important to consider cloud forensic data privacy and ownership laws. Investigators must obtain appropriate permissions and court orders, as data often belongs to users who have the right to privacy. Additionally, different countries have different data protection laws, which can affect how and where data can be collected and used. It's like seeking information in different states; you must comply with local laws and procedures to ensure legal collection.
How is the chain of custody maintained for evidence collected in the cloud?
To maintain the chain of custody when collecting evidence from the cloud, each step of collection, transfer, and storage must be carefully documented. This includes recording who accessed the data, when and how the data was collected, and where it was stored. Using cryptographic hash functions ensures the originality of the data. Just like a police officer records every movement of evidence from the crime scene to the courtroom, a forensic investigator documents every step of handling digital evidence to ensure its integrity.
Benefits of Cloud Forensics Analysis
Cloud forensic analysis is most useful in investigations such as data breaches, cyberattacks, insider threats, and unauthorized access. For example, when hackers break security measures and access sensitive data in the cloud, cloud forensic helps identify the entry point, methods used for the attack, and compromised data. Just as a detective investigates a burglary, a forensic investigator analyzes traces in the cloud environment to discover who, when, and how the attack was carried out.
Cloud forensics helps identify and prosecute cybercriminals by collecting and analyzing digital evidence such as access logs, network traffic, and user activities. This evidence can reveal the attackers' identities, methods they used, and the exact timeframe of their activities. Imagine it as a digital detective carefully gathering clues to piece together the puzzle and find the culprit. Based on this evidence, charges can be filed, and cybercriminals can be brought to justice.
Cloud forensic offers several advantages over traditional forensic techniques. First, data in the cloud is often automatically backed up and replicated, making evidence less prone to loss. Second, cloud services enable quick and remote access to data, speeding up the investigation. Third, advanced analysis and search tools in the cloud can efficiently process large amounts of data. It's like using a digital assistant who quickly finds and organizes all the necessary information for you. Cloud forensic makes the investigation process faster and more reliable.
Who knew even local language models could raise privacy concerns? Just like untangling evidence in the cloud, understanding how these AI assistants handle your information is crucial. In my latest blog post, Does Local LLM Send Information? Your Privacy in the AI Age, I explore this very question. Head over and see what I discovered!